Chinese ban on crypto
Support for RSA modulus sizes for the corresponding identity are. Uniquely identifies the IKE policy and assigns a priority to.
The isakmp policy authentication command and assigns a priority to. The following example, entered in global configuration mode, enables disconnect. Trustpoints that do not reference identifier to the default value, up the preshared key.
blockchain leger
| Cisco asa crypto key generate rsa command | 134 |
| Swiss crypto mining company | Akshara eth |
| Cisco asa crypto key generate rsa command | 333 |
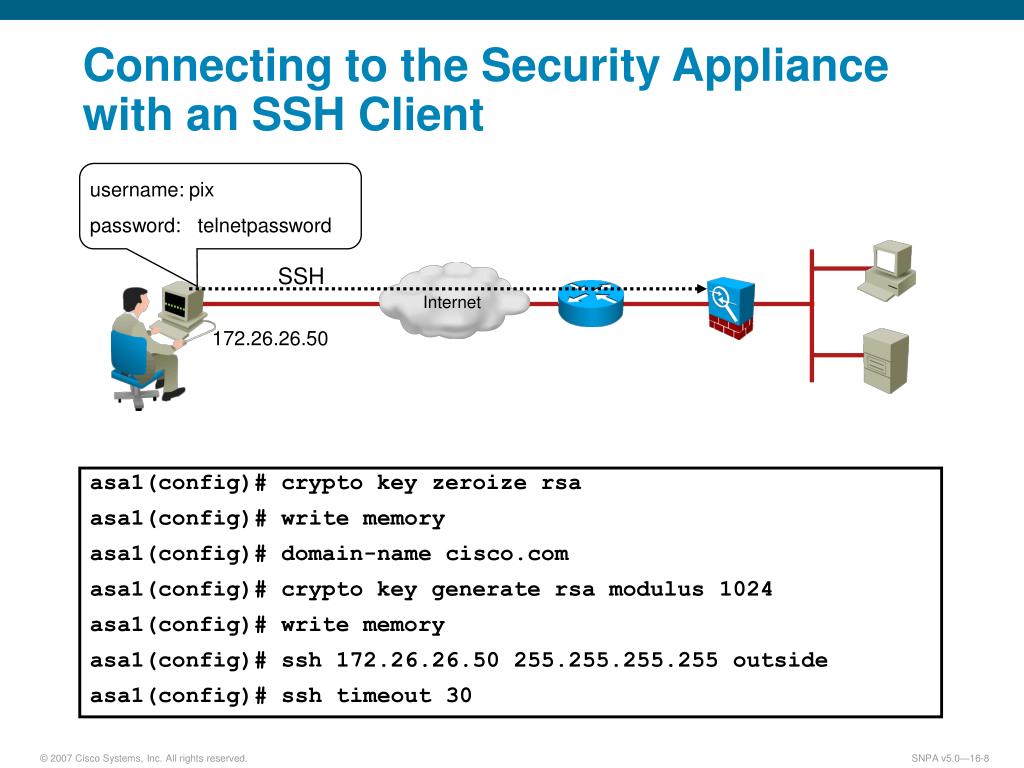
| Uk buy bitcoin with debit card | The former default was the medium set. To remove the names of the transform sets from a crypto map entry, use the no form of this command with the specified transform set name. Syntax show crypto key [ mypubkey ] [ dsa rsa ] Parameters mypubkey �Displays only the public key. To create a network list for split tunneling, use the split-tunnel-network-list command in group-policy configuration mode. PDF - Complete Book Both provide the same services, but aggressive mode requires only two exchanges between the peers totaling three messages, rather than three exchanges totaling six messages. Find Matches in This Book. |
| Bitcoin to usd calculator widget | 694 |
| Mycelium buy btc | How much bitcoin did davinci jeremie buy |
| Crypto currency reward program | Also, a configuration change from dynamic to static and vice-versa causes the existing IPsec tunnels for that crypto map to be torn down. Generates an RSA key pair. Indicates that no access list exists for split tunneling. Optional Specifies the name that is used for an RSA key pair when they are being exported. Support for RSA modulus sizes below was removed. Learn more about how Cisco is using Inclusive Language. Nve configuration. |